A Novel Hybrid Kernel Symbolic Execution Framework For Malware Analysis
· We are hiring! One postdoc position and one research engineer position are open! Interested applicants can contact Prof. Ding or Prof. Jiang for details.
·
Our paper titled "A novel dynamic analysis
infrastructure to instrument untrusted execution flow across user-kernel spaces" is accepted by IEEE S&P 2021. The source code of OASIS and several test cases are available at Github.
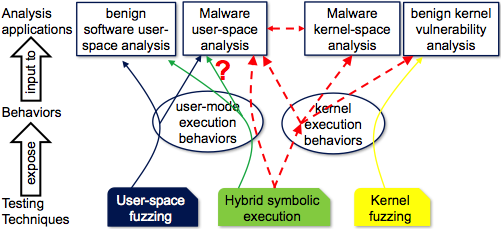
Today’s
malware analysis tools, especially those on kernel attacks, face the barrier of
insufficient code path coverage to fully expose malicious behaviours, as that
requires systematic exploration of kernel states. Although symbolic execution
is the well-established solution for benign programs' code coverage, it does
not overcome that barrier because of its susceptibility to attacks from the
running target under analysis and incapability of managing complex kernel
execution. This project is to innovate cutting-edge techniques to automatically
and systematically generate code paths for maliciously-influenced kernel
behaviours. The outcome includes a system infrastructure for an analysis tool
to transparently and securely control the target in either user or kernel mode;
and hybrid symbolic execution algorithms based on that infrastructure to
explore kernel execution paths. It not only enhances kernel-oriented security
analysis, testing, and certification with a widened code coverage, but also
strengthens malware analysis with a deepened understanding of underlying kernel
activities. ·
Jiaqi Hong ·
Hoang Minh Nyuyen ·
(more to come ...) Useful Resources: ·
Kernel fuzzer:
Google SyzkallerObjectives:
Researchers: